Iso 27001 Information Security Policy Template - Vendor managementsoc 2 security reports For example, “all access to sensitive systems will be logged and monitored. It includes policies, procedures, and processes designed to manage information. Vendor managementsoc 2 security reports Iso 27001 is a widely used security standard that lays out how to build an effective. This repository provides an iso 27001:2022 toolkit,.
Vendor managementsoc 2 security reports It includes policies, procedures, and processes designed to manage information. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,. For example, “all access to sensitive systems will be logged and monitored.
Iso 27001 is a widely used security standard that lays out how to build an effective. For example, “all access to sensitive systems will be logged and monitored. Vendor managementsoc 2 security reports It includes policies, procedures, and processes designed to manage information. Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,.
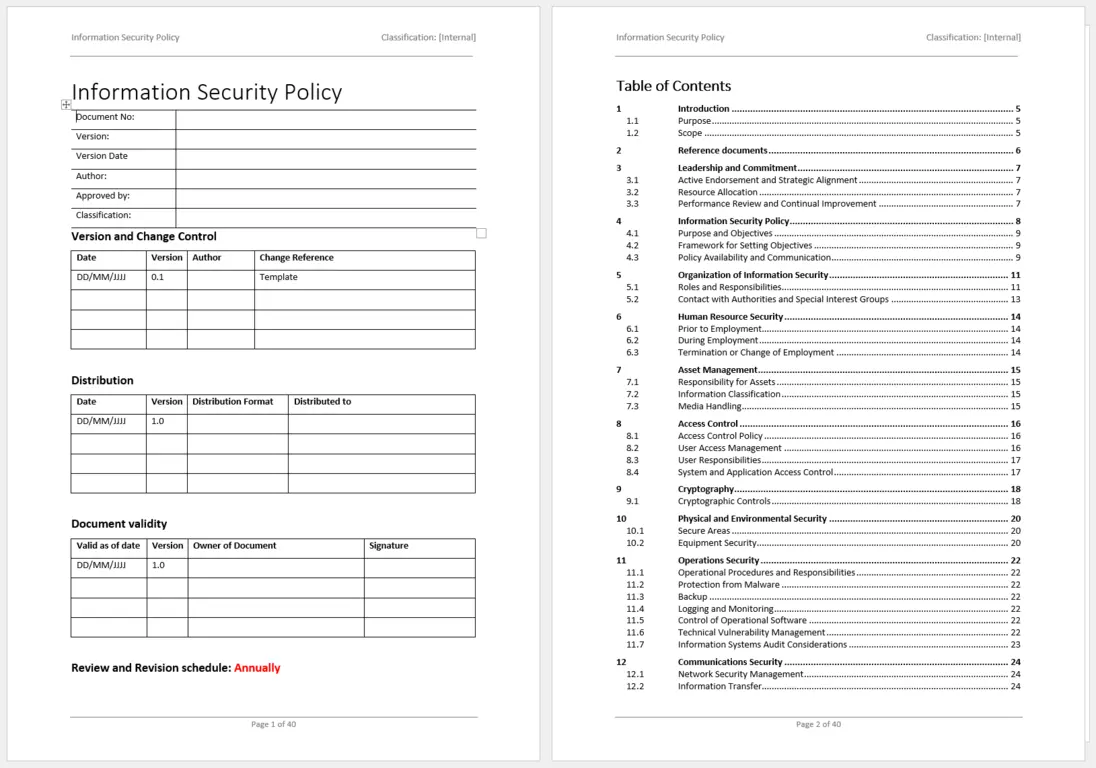
Information Security Policy Template Iso 27001
This repository provides an iso 27001:2022 toolkit,. For example, “all access to sensitive systems will be logged and monitored. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports Vendor managementsoc 2 security reports
ISO 27001 Information Security Policy Word Template ISO Templates and
Iso 27001 is a widely used security standard that lays out how to build an effective. It includes policies, procedures, and processes designed to manage information. Vendor managementsoc 2 security reports Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,.
ISO 27001 Information Security Policy Template Secureframe Secureframe
Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,. For example, “all access to sensitive systems will be logged and monitored. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports
Iso 27001 Policy Templates Printable Word Searches
Vendor managementsoc 2 security reports It includes policies, procedures, and processes designed to manage information. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,.
Free ISO 27001 Checklists and Templates Smartsheet
For example, “all access to sensitive systems will be logged and monitored. Vendor managementsoc 2 security reports This repository provides an iso 27001:2022 toolkit,. It includes policies, procedures, and processes designed to manage information. Vendor managementsoc 2 security reports
ISO 27001 Information Security Policy Ultimate Guide [+ template]
It includes policies, procedures, and processes designed to manage information. Vendor managementsoc 2 security reports For example, “all access to sensitive systems will be logged and monitored. This repository provides an iso 27001:2022 toolkit,. Iso 27001 is a widely used security standard that lays out how to build an effective.
Iso 27001 Information Security Policy Template PDF Template
Vendor managementsoc 2 security reports It includes policies, procedures, and processes designed to manage information. Iso 27001 is a widely used security standard that lays out how to build an effective. For example, “all access to sensitive systems will be logged and monitored. This repository provides an iso 27001:2022 toolkit,.
Download An ISO 27001 Information Security Policy Template
For example, “all access to sensitive systems will be logged and monitored. This repository provides an iso 27001:2022 toolkit,. It includes policies, procedures, and processes designed to manage information. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports
The Ultimate ISO 27001 Information Security Policy Template
Vendor managementsoc 2 security reports Vendor managementsoc 2 security reports For example, “all access to sensitive systems will be logged and monitored. This repository provides an iso 27001:2022 toolkit,. Iso 27001 is a widely used security standard that lays out how to build an effective.
Iso 27001 Security Policy Template
This repository provides an iso 27001:2022 toolkit,. Vendor managementsoc 2 security reports It includes policies, procedures, and processes designed to manage information. Iso 27001 is a widely used security standard that lays out how to build an effective. Vendor managementsoc 2 security reports
For Example, “All Access To Sensitive Systems Will Be Logged And Monitored.
Vendor managementsoc 2 security reports Iso 27001 is a widely used security standard that lays out how to build an effective. This repository provides an iso 27001:2022 toolkit,. Vendor managementsoc 2 security reports




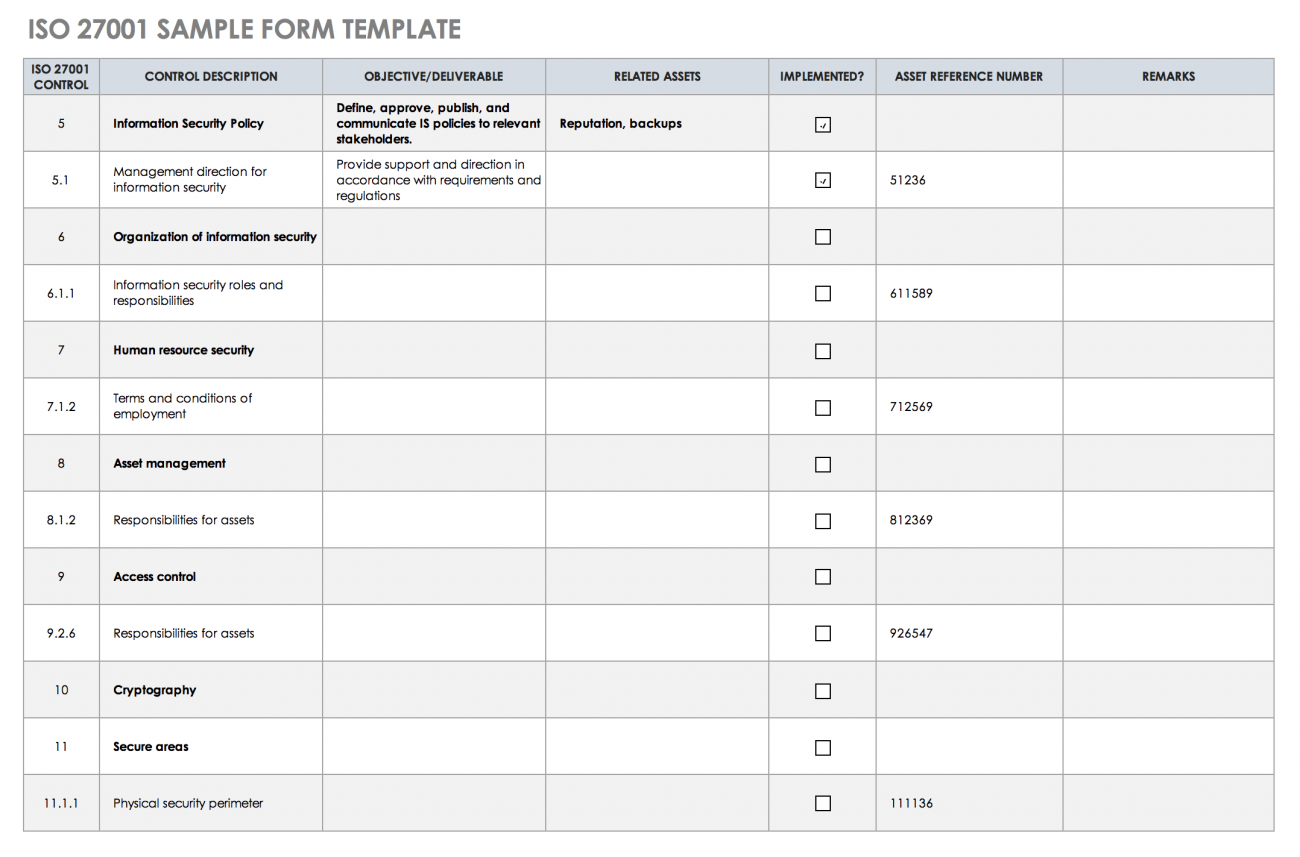
![ISO 27001 Information Security Policy Ultimate Guide [+ template]](https://hightable.io/wp-content/uploads/2022/10/ISO27001-Information-Security-Policy-Example-1-719x1024.png)